What are the key components for implementing SD-WAN in the high-security sector?
High-performance wide-area networks hinge on advanced edge technology and open, software-centric solutions. Discover expert best practices for implementing a resilient, future-proof SD-WAN in the high-security sector.
Thomas Schneider

Reduce edge complexity with SD-WAN
A property connects to other properties or the cloud via a wide area network (WAN). Various bandwidth services can be used such as Layer 1 DWDM services, Layer 2 Ethernet leased lines, MPLS-based services like IP-VPNs and virtual private wire services (VPWS) or protected internet tunnels. Each technology option uses a dedicated access device that can be redundantly connected to the WAN for high availability. Adapting these hardware-centric solutions to new requirements is a complex challenge.
With SD-WAN technology, essential functions at network access points are implemented as software functions complemented by enhanced security features. This allows easy adaptation to any WAN technology and different redundancy concepts. Data traffic can be transmitted performance-optimized by application-specific routing providing the best path in the WAN network. In the event of a link network failure, traffic is transmitted with prioritization over the remaining channels. Furthermore, SD-WAN provides extensive monitoring and performance management capabilities, enabling efficient, secure and robust use of the wide area network.
Operators with high-security requirements tend to prefer private clouds for hosting and wavelength or Ethernet services for connectivity, avoiding the significantly larger attack surface of internet tunnels.
SD-WAN implementation best practices
Virtualization of network functions (NFV, network functions virtualization) complements the introduction of SD-WAN as an open and expandable access technology. Network functions that were previously implemented as hardware can now be realized as software on commercial servers. Established network access and protection technology manufacturers offer a wide range of virtualized network functions (VNF), for example, SD-WAN, firewalls, routers or intrusion detection systems.
Since network access devices are often operated outside highly secured IT areas and data centers, the device’s protection is particularly important. It must be safeguarded against attacks from the connection network, which can also occur on the lower network layers and against physical attacks. The solution developed by Adva Network Security has been optimized for this application.
Our FSP 150-XG118Pro (CSH) has extensive monitoring functions to ensure high availability. Software applications can be hosted on an integrated, standard server running a hardened network operating system (NOS). The integrated server is comprehensively protected against attacks by hardware-based L2 encryption and physical tamper protection. This modular network access device has already proven itself in practice many times over and has been approved by the BSI to transmit classified data. The DWDM-capable network interfaces enable efficient use of the optical fiber in the access network.
As the connectivity network is well protected by certified security technology, the network access device with hosted network functions can be applied with classified data.
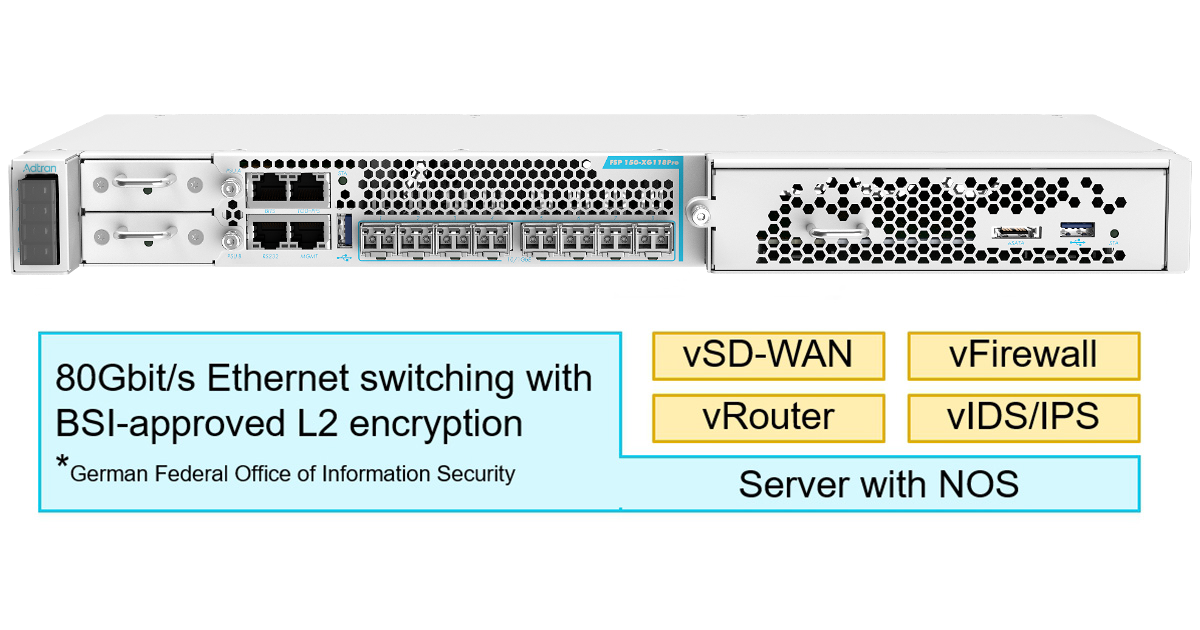
FSP 150-XG118Pro (CSH) with integrated server for hosting virtualized network functions
Multi-vendor design for unprecedented flexibility and future-proofing
Our universal CPE (uCPE) can host software applications from many vendors and be used in many application scenarios. An operator can quickly introduce new features using VNFs or activate third-party NFV products with a single mouse click.
The network access sector has been characterized by rapid innovation cycles in recent years. Secure Access Service Edge (SASE) expands on recently established SD-WAN technology by integrating zero-trust security principles, which call for the adoption of new features such as micro-segmentation in next-generation firewalls, policing or authentication. In this very dynamic environment, open network technology offers significant advantages.
Through interoperability tests, we ensure that NFV products from many manufacturers are compatible with our solution. VNFs from several suppliers have been tested on our platform and some are already in commercial use. A comprehensive overview of the VNFs supported by Adtran’s Ensemble Harmony Ecosystem is published on the website.
Our powerful Ensemble management system offers comprehensive control and monitoring of the VNF-hosting infrastructure, including management and orchestration (MANO) capabilities.
Summary
With NFV technology, SD-WAN offers the flexibility to react efficiently and quickly to new requirements, such as zero-trust architecture and SASE. The network access technology deployed must be robust and scalable, providing extensive monitoring and protection functions. Our FSP 150-XG118Pro (CSH) was designed for this application and is approved by the BSI. It supports a wide range of VNFs on its integrated server, which runs the proven and reliable Ensemble Connector network operating system.


