How crucial are trusted wide area networks for zero trust architectures?
As mobile work and cloud hosting rise, IT access often bypasses secured perimeters, weakening traditional security measures. Zero trust networks address this security void, but the lack of standardization and clarity is a challenge. Let’s debunk some misconceptions.

Implicit trust based solely on physical location within a secured perimeter is inadequate for the security demands of today’s mobile workforce and cloud hosting. As zero trust (ZT) emerges as the new paradigm for secure network architectures, it’s essential to set realistic expectations. While ZT is pivotal, it should not be considered the silver bullet that renders all previous security controls obsolete. Nor should it be misunderstood as a way to achieve security without trust. Some misconceptions about ZT are widespread, and it's high time we address them. Let’s begin …
Does zero trust mean security without trust?
The zero trust paradigm suggests handling entities inside and outside a protected perimeter in the same way. This is a sensible approach as it meets the requirements of a changing threat landscape and also limits the negative impact of malicious insiders and rogue devices. In a zero trust architecture, any access to resources mandates authentication and authorization of an entity, regardless of its physical location.
However, while the “never trust, always verify” mantra sounds definitive, it can loop into circular reasoning. Verification of trust results in a need to rely on credentials or certificates from the next level in a trust hierarchy. For instance, the verification of the identify will require confidence in the software confirming the password as well as in the secure storage mechanisms like high-security modules (HSM) or trusted platform modules (TPM). In short, each verification step pushes the need for trust to a different level of the chain, which might trigger a need for further verification until the final trust anchor is reached.
In my view, the term “zero trust” is misleading. Implementing a zero trust network architecture requires a thorough analysis of trust dependencies and assessment of confidence levels.
Do zero trust architectures make perimeter protection obsolete?
As entities both inside and outside a perimeter-protected environment are secured with zero trust principles, perimeter protection might be seen as obsolete. This, however, is a risky view, here comes why.
Zero trust principles were initially triggered by an increase in mobile workers and cloud hosting. In both cases, the entities are outside the perimeter-protected IT network. Here zero trust is an invaluable and mandatory security control.
On the other hand, there are many use cases with devices and users located on a corporate site where perimeter protection remains invaluable:
Defense in depth: Even if one security control fails or verification is compromised, multi-layered security architectures, known as “defense in depth,” enhance network robustness. Zero trust architectures should be bolstered with additional security measures.
Device limitations: Not all devices, especially simpler IoT devices, can support robust authentication and protection mechanisms. For these, a perimeter-based security approach offers a more efficient defense mechanism.
Network-inherent capabilities: Relying solely on end-point protection can overlook built-in network security features like segmentation, port-filtering, encryption and policy enforcement. Leveraging the wider network can minimize potential threats and enhance overall security.
Trusted networking favorably complements ZT architectures
Zero trust does not mean that security can be achieved without trust, or that perimeter protection will no longer be needed. Instead, it is about understanding whom to trust, and focusing on authentication, authorization and reducing attack surfaces through segmentation. That’s why network-provided security features are indispensable in robust zero trust architectures.
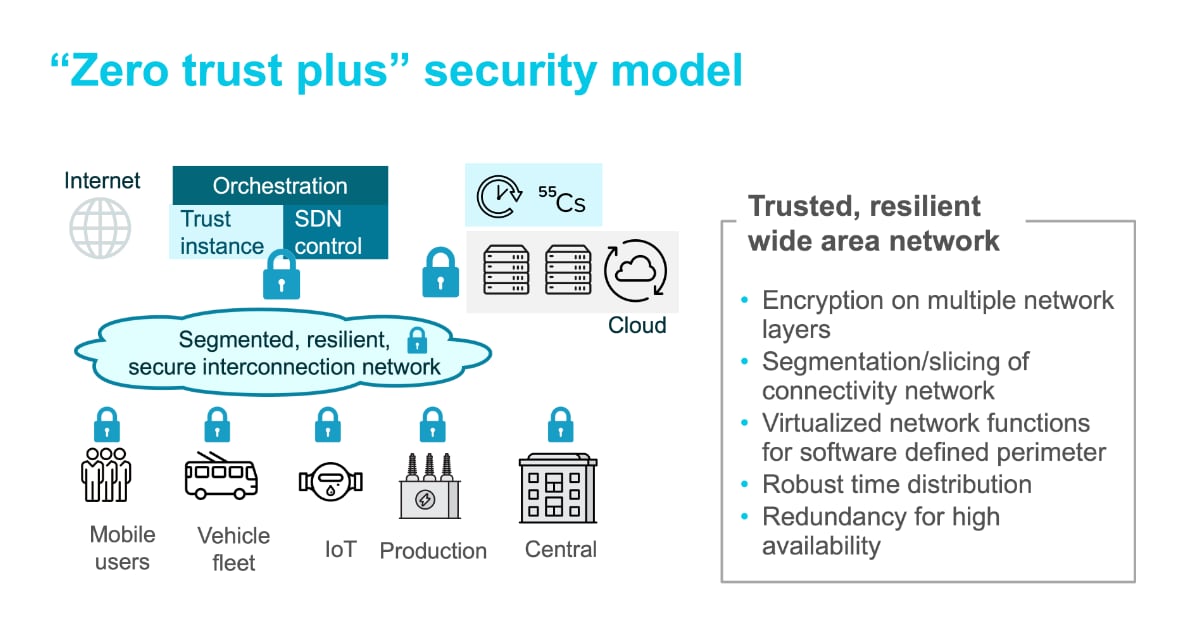
The number of entities operated on a corporate site such as a power station or chemical plant can be quite significant. It is good security practice to segment devices into application domains and jointly protect those domains with a common security perimeter. The connecting network should complement these security control by keeping traffic separated and protected. Separation, often called “slicing”, could be implemented by VLAN, OTN or MPLS technologies. In addition, end-to-end quantum-safe encryption in combination with policy control should be provided for each connection.
The below graphic shows a zero trust network architecture with trust instances for authentication and policy management in combination with an SDN control for activation of end-to-end encrypted and sliced network connections.