Is efficient use of quantum keys the cornerstone of cryptographic safety?
As the looming threat of quantum computers challenges traditional key exchange, the spotlight shifts to QKD. Having proven its worth in numerous demos, the focus is now on real-world QKD implementation. Yet, with limitations in range and key generation rate, the pressing question remains: How can we maximize the efficiency of quantum keys?
Mario Wenning

Using quantum technologies for key distribution is a promising way to counter the emerging quantum threat. While this technology can provide information-theoretic security, quantum key distribution builds on the exchange of information using quantum states, requiring the detection of deficient power levels. Due to this, the distance of quantum key transport is limited, and the number of securely delivered quantum keys is moderate. Let’s look at the limitations of quantum key distribution and propose solutions for practical deployment.
The quantum channel and secret key rates
A QKD system comprises a quantum bit generator and a remote qubit receiving device. A quantum channel and a classical communication channel connect both devices. The quantum channel is solely used for exchanging qubits. As eavesdropping impacts the quantum state, attacks can be detected by a communication protocol such as “prepare and measure” over the classical link. Such postprocessing enables the devices at both endpoints to eliminate compromised quantum data. The remaining information is a quantum-safe secret, which can be used as session keys with quantum-safe symmetrical encryption algorithms such as AES-256.
The quality of the quantum channel bounds the rate of secure key generation, i.e., the secret key rate (SKR). With increasing distance and attenuation, the SKR decays exponentially until the maximum length is reached. For bridging longer distances, either a quantum repeater or a trusted node (TN) is needed. Quantum repeaters are still not practically applicable. TNs need stringent physical access controls as quantum-safe keys are processed at those nodes in clear text.
How many quantum keys do we need?
Let’s assume a hypothetical QKD system that protects a DWDM link with 80 optical channels transporting 400Gbit/s each. At such high speeds, the keys for each optical link should be renewed every minute. In consequence, the system has a key consumption rate of 80 keys per minute for each direction. As each key has a length of 256 bits, we need approximately 683bit/s.
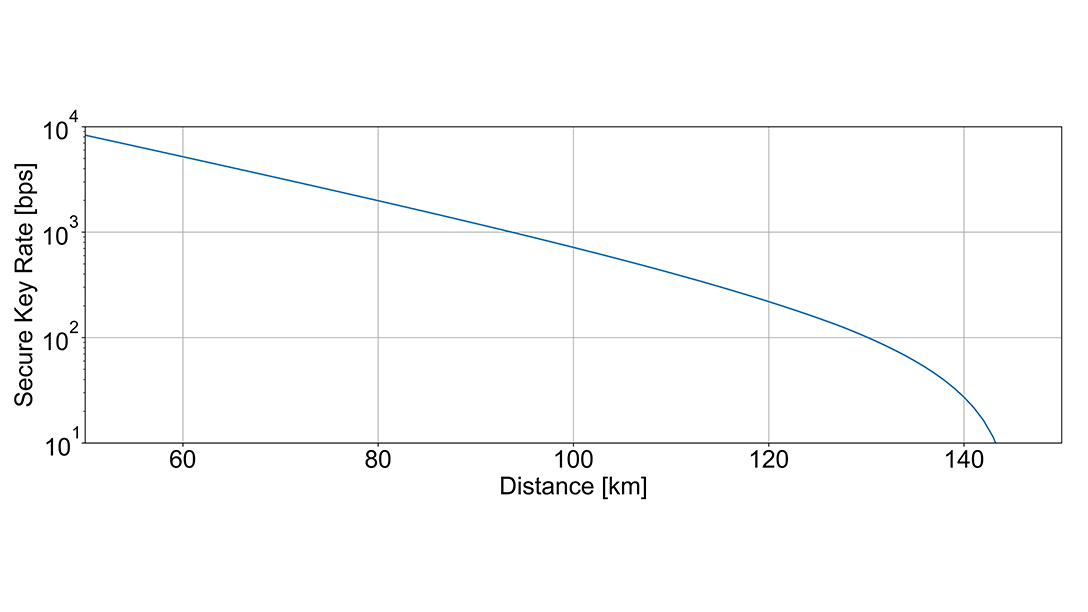
As discussed, the secret key rate of QKD systems is moderate. The diagram above illustrates an exemplary exponential decay, showing the secret key rate as a function of attenuation. Shorter links with lower attenuation enable QKD systems to provide more secret keys than longer links and higher attenuation. In our example, a system requiring approximately 700 bit/s for its secret key rate could span a distance of 110km.
This leads to an important question: How can we design a QKD network to ensure an adequate supply of encryption keys while minimizing the number of QKD devices and TNs?
Optimizing consumption of QKD keys
When designing a DWDM network that utilizes QKD keys, two essential considerations emerge:
- Endpoint key delivery: QKD delivers quantum-safe key material to the endpoints of a repeaterless hop. In practical networks, optical links span several hops with encryptors at the endpoints. This means that the need for keys isn't dictated by individual hops, but rather by the entire optical connection.
- Network resilience with mixed routes: Resilient DWDM networks are designed with alternative routes connecting their sites, consisting of both short and long links. As outlined above, QKD systems with lower attenuation can deliver a higher secret key rate, making them especially suitable for shorter links.
We developed an optimization algorithm that minimizes cost.
Consequently, the DWDM system and the QKD network should be considered separate service layers. The routing of the light path and the topology of the DWDM system is not necessarily the same as the delivery of the keys and the topology of the QKD network. The architecture supports key demand grooming and efficient key distribution, preferring shorter-distance QKD hops. In turn, this helps supply longer hops with the necessary secret material.
We developed an optimization algorithm that minimizes cost by jointly optimizing key relaying and QKD network deployment. Our algorithm uses fiber topology and DWDM characteristics such as channel count and resiliency requirements as input. It calculates the required number of QKD devices and their placement in the network and defines how QKD-delivered keys are provided to the endpoints of the optical connections.
Studies of topologies from DWDM systems show that our optimized approach leads to substantial savings in the number of QKD devices and trusted nodes compared to less efficient deployment strategies. By using global optimization, we can not only minimize costs by reducing the number of QKD devices but also enhance security by limiting the number of trusted nodes, thus decreasing potential attack points.
Outlook and summary
As we advance in designing QKD solutions for real-world deployment, the need to optimize the consumption of QKD keys has become increasingly evident. A significant cost reduction can be achieved by leveraging the higher-key delivery capacity of shorter QKD hops. These results have been verified theoretically and practically, providing an essential improvement to previous QKD network designs.
